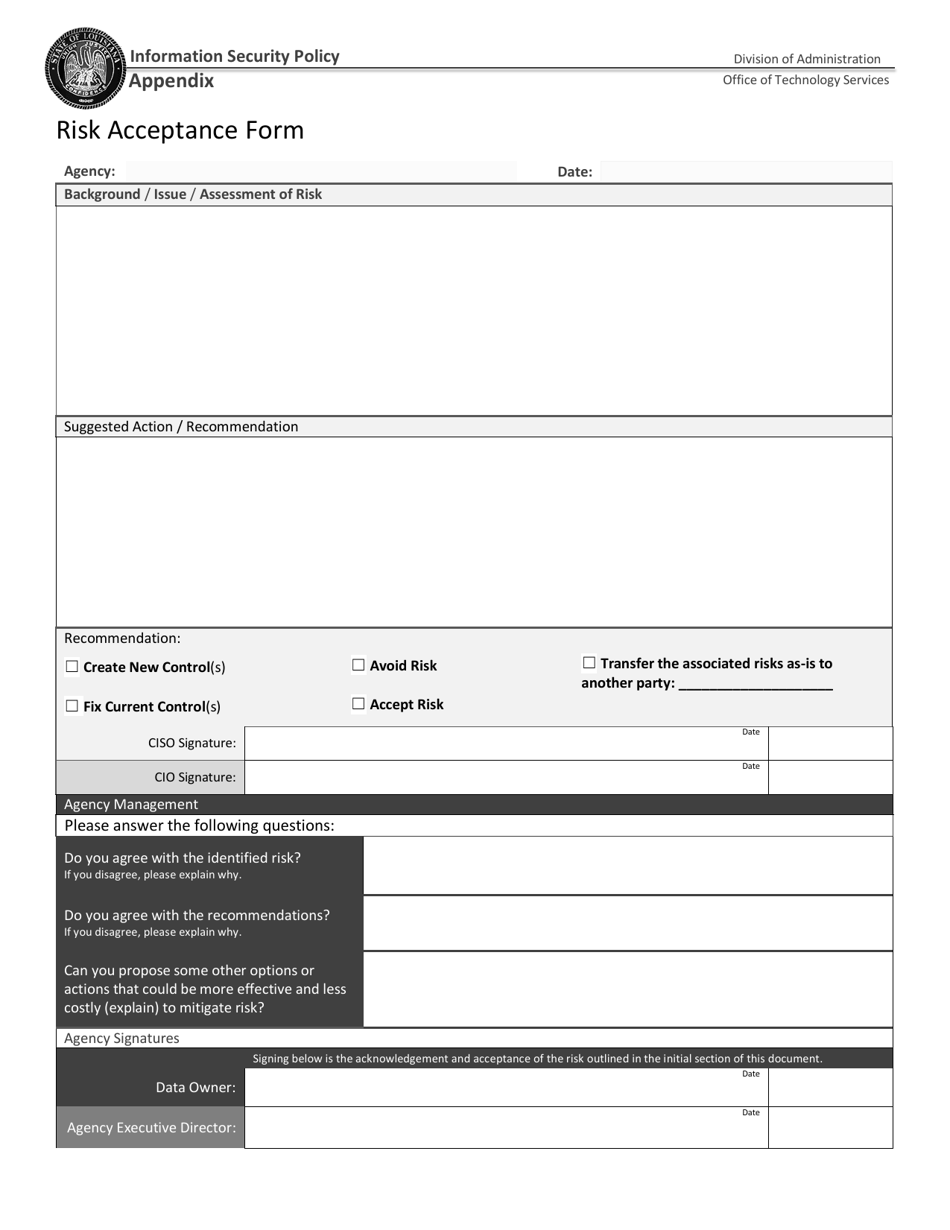
Risk Acceptance Form - A form to justify a risk acceptance of a known deficiency in a system or project. It requires a compensating control, a justification, and. A form for requesting and accepting exceptions to information security policies and standards at ohio university. Use this form to assess.
It requires a compensating control, a justification, and. Use this form to assess. A form for requesting and accepting exceptions to information security policies and standards at ohio university. A form to justify a risk acceptance of a known deficiency in a system or project.
A form for requesting and accepting exceptions to information security policies and standards at ohio university. It requires a compensating control, a justification, and. A form to justify a risk acceptance of a known deficiency in a system or project. Use this form to assess.
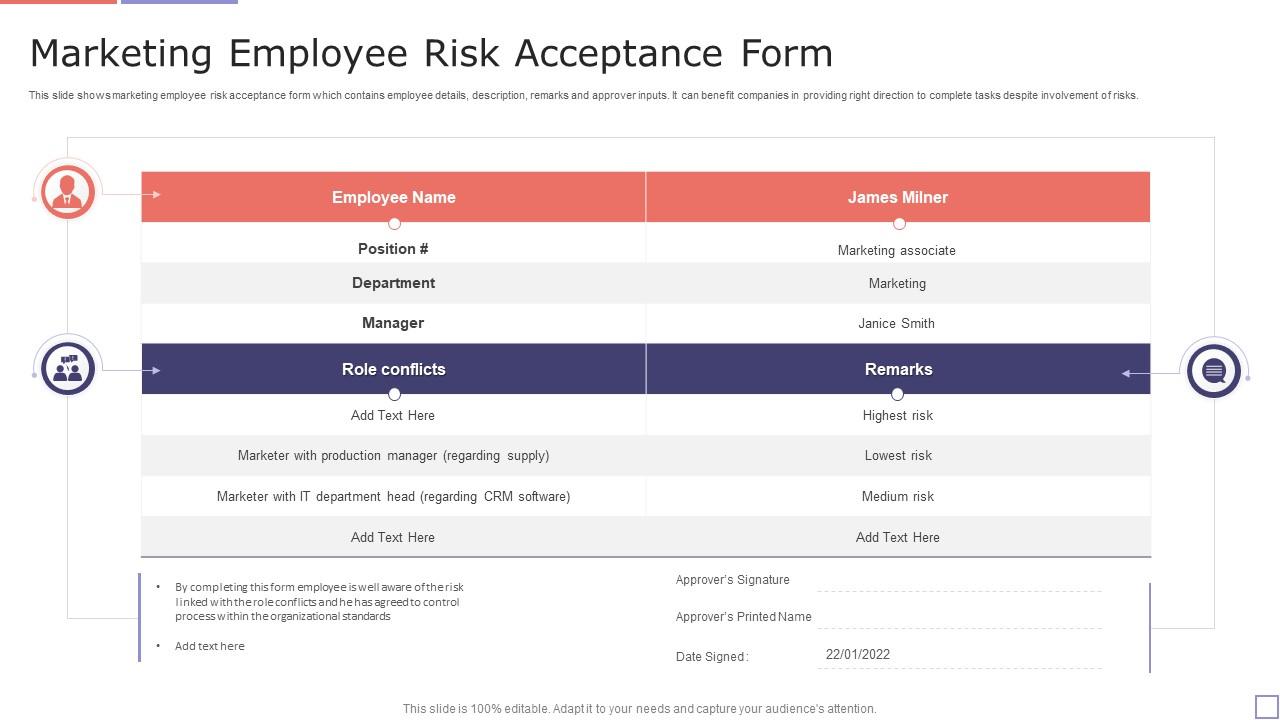
Marketing Employee Risk Acceptance Form
A form for requesting and accepting exceptions to information security policies and standards at ohio university. Use this form to assess. It requires a compensating control, a justification, and. A form to justify a risk acceptance of a known deficiency in a system or project.
Risk Acceptance Form — RCFL
Use this form to assess. A form for requesting and accepting exceptions to information security policies and standards at ohio university. A form to justify a risk acceptance of a known deficiency in a system or project. It requires a compensating control, a justification, and.
FREE 37+ Risk Assessment Forms in PDF MS Word
A form to justify a risk acceptance of a known deficiency in a system or project. Use this form to assess. A form for requesting and accepting exceptions to information security policies and standards at ohio university. It requires a compensating control, a justification, and.
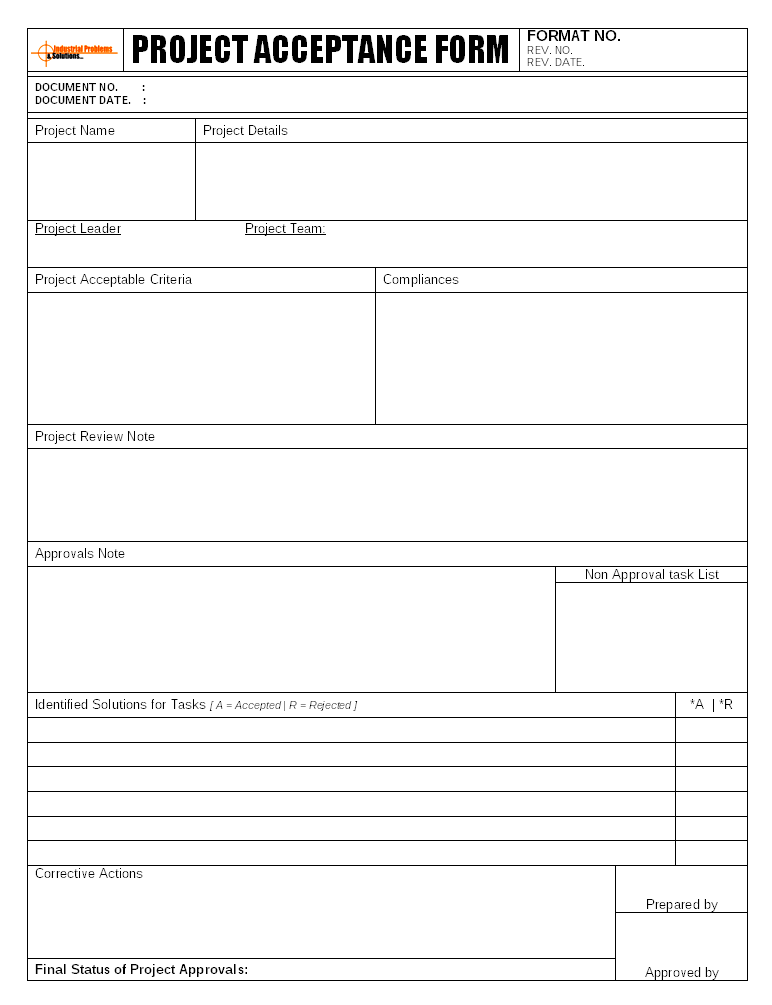
Project review and acceptance process
Use this form to assess. A form for requesting and accepting exceptions to information security policies and standards at ohio university. It requires a compensating control, a justification, and. A form to justify a risk acceptance of a known deficiency in a system or project.
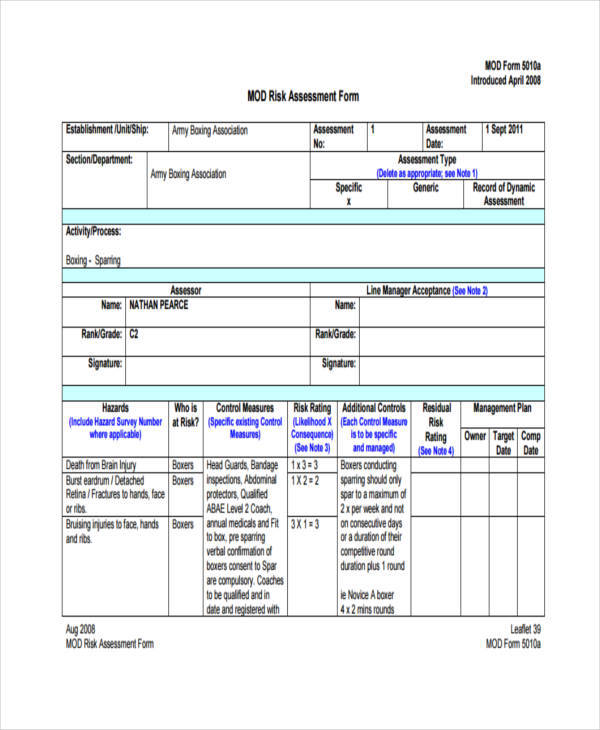
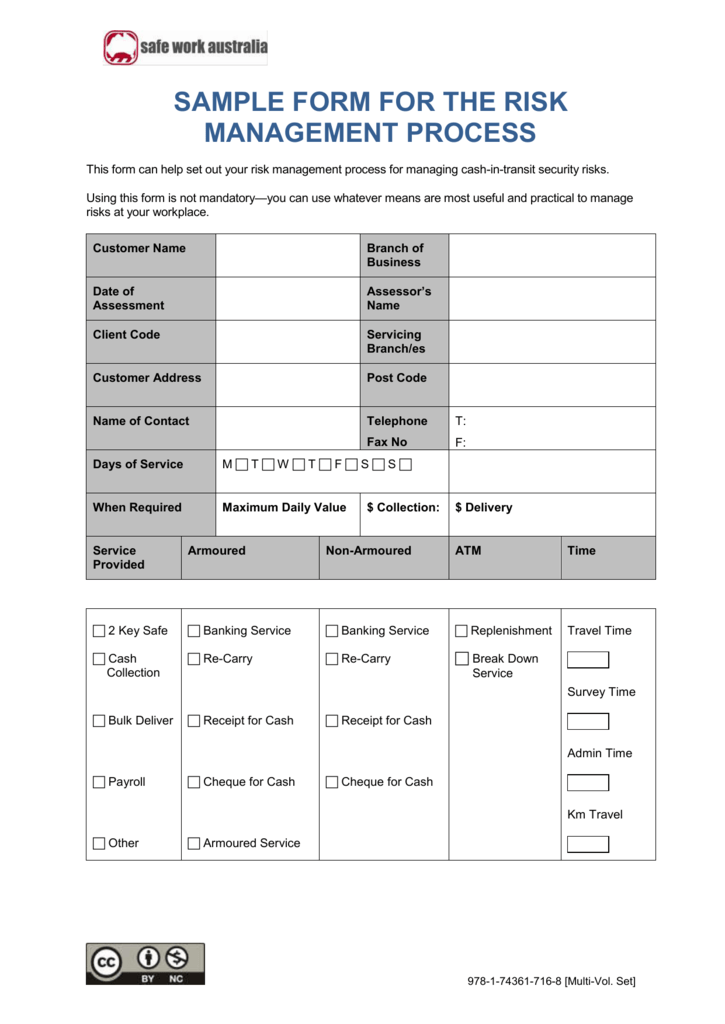
5. Sample form for the risk management process
Use this form to assess. A form for requesting and accepting exceptions to information security policies and standards at ohio university. It requires a compensating control, a justification, and. A form to justify a risk acceptance of a known deficiency in a system or project.
Louisiana Risk Acceptance Form Fill Out, Sign Online and Download PDF
A form for requesting and accepting exceptions to information security policies and standards at ohio university. It requires a compensating control, a justification, and. A form to justify a risk acceptance of a known deficiency in a system or project. Use this form to assess.
Risk Acceptance Form Template Jotform
A form to justify a risk acceptance of a known deficiency in a system or project. It requires a compensating control, a justification, and. A form for requesting and accepting exceptions to information security policies and standards at ohio university. Use this form to assess.
Accessing Risk Acceptance Template Form
A form for requesting and accepting exceptions to information security policies and standards at ohio university. Use this form to assess. It requires a compensating control, a justification, and. A form to justify a risk acceptance of a known deficiency in a system or project.
Risk Acceptance Form Threat Vulnerability
A form for requesting and accepting exceptions to information security policies and standards at ohio university. A form to justify a risk acceptance of a known deficiency in a system or project. Use this form to assess. It requires a compensating control, a justification, and.
Information Risk Acceptance Process
It requires a compensating control, a justification, and. Use this form to assess. A form for requesting and accepting exceptions to information security policies and standards at ohio university. A form to justify a risk acceptance of a known deficiency in a system or project.
A Form To Justify A Risk Acceptance Of A Known Deficiency In A System Or Project.
A form for requesting and accepting exceptions to information security policies and standards at ohio university. It requires a compensating control, a justification, and. Use this form to assess.